Why State of the Art (SOTA) security for the IoT market relies on the SESIP methodology
By Carlos Serratos, IoT Certification Expert at NXP
Following on from his previous blog which delved into the detail concerning the evolution of European regulations – and how SESIP can support the IoT ecosystem – Carlos Serratos, IoT Certification Expert at NXP, focuses on State of the Art (SOTA) technology and why certification is critical for the future of secure solutions.
The State of the Art (SOTA) security functionality is not defined as the ‘latest or greatest’ in security technology, but one that provides contra-measure mechanisms which are proportional to the risk. While this is easy to say, for a long time it has been a difficult challenge to address for the whole industry, as requirements for IoT devices vary from the most basic, to advanced levels of security – which is a key driver behind the development of the Security Evaluation Standard for IoT Platforms (SESIP) methodology.
On one hand, IoT device manufacturers’ expertise often focuses on different domains that are outside the security functionality. For example, in the case of an IP video camera; the developer might be an expert in digital image processing, compression and analytics, but there is also an intrinsic need to protect this data at rest, and in transit. Core security capabilities – like encryption, secure storage, and platform isolation – tend to be out of the domain of IoT innovators, who specialize in specific markets/solutions, and variations of this product might address home use, as well enterprise use and even public administration surveillance. In short, this example can be defined as being a SOTA solution for consumer applications because it might not meet the level of ‘acceptance’ for SOTA under another application with a higher risk level.
On the other hand, suppliers of components are challenged with supporting the statement: “trust me, my product is secure.” The device manufacturer might be asking this question to each supplier and receiving similar answers. However, the definition of ‘secure’ could vary from one use case to another. Is it to do with secure storage or encryption, for example? And how secure is ‘secure enough’? Even more importantly, what use case is this component providing SOTA security capabilities for? Each of these will impact the requirements of the device.
In a previous blog, we addressed the emergence and demand for security functionalities for IoT devices, and the SOTA approach is a very common one. That is because a regulators’ role is to make sure there is a level playing field for all those in a particular ecosystem to prevent a user’s trust becoming eroded over time due to the lack of security, which can leave them vulnerable and at a higher risk of costly cyberattacks. Since each ecosystem is different, the expectations of the security functionality are also very different. Therefore, the SOTA reference is an excellent metric to understand when ‘good’, is ‘good enough’.
Introducing the five SESIP levels
SESIP provides clear definitions concerning the security functionality on components and platforms, in the form of Security Functional Requirements (SFRs). It also provides strength metrics (robustness against attacks) in the form of SESIP ‘levels’ (see diagram below).
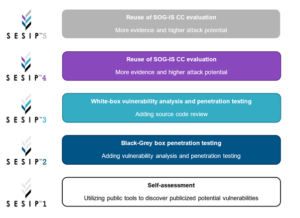
These levels are perfectly aligned with internal security standards like Common Criteria class (AVA_VAN), or vulnerability analysis. Moreover, SESIP can be applicable to show resistance against different vectors of attack including:
- Remote attacks
- Logical attacks
- Physical attacks
- Or a combination of them all.
This gives developers a clear understanding what is behind the subjective claims of ’secure’ products.
For IoT device manufacturers, visibility of the security capability present on the components and platform allows them to identify which one is the right fit-for-purpose – ultimately matching the SOTA capabilities against their specific use cases. Moreover, when it comes to demonstrating the SOTA capability of their own products – when such capability is coming from the components or platforms like cryptography, for example – SESIP provides the evidence and metrics to prove this statement.
As technology evolves, the volume and sophistication of threats also continue to keep apace. So, what is SOTA today might not be the same tomorrow. Having visibility and understanding of the core security functionality is critical for ecosystems when selecting the fit-for-purpose solutions. SESIP is designed with such philosophy in mind.
If you want to know more about SESIP, security regulatory compliance and the latest trends in those areas, revisit GlobalPlatform’s recent seminar in Barcelona, and don’t forget to join us online or in-person for the next SESIP seminar which will be held in Taipei, Taiwan on November 30, 2022.

