What Role will SESIP Play in the EUDI Wallet Ecosystem?
In a previous blog, GlobalPlatform introduced the European Digital Identity (EUDI) Wallet, to explore the challenges for the 27 EU member states to implement their schemes and explain how it can support the deployment of digital identity solutions across Europe.
In this blog, NXP Security Certification Expert, Fabien Deboyser, explores the key considerations for the certification of EUDI Wallets. Fabien reviews the specifics of mobile phone architecture aligned with the latest Architecture and Reference Framework (ARF) provided by the eIDAS expert working group, outlines envisioned use cases, provides analysis on the key challenges for security certification and defines the role of the Security Evaluation Standard for IoT Platforms (SESIP) methodology.
Mobile phone architecture & the eIDAS expert working Group ARF
Mobile phones have become an essential part of our lives and we use them for a variety of purposes, including communication, online banking, shopping, transportation, social media and many more. The architecture of a mobile phone is complex, involving a variety of hardware components (e.g. processor, sensor, display, battery, camera) and software components (e.g. Operating Systems, applications, drivers, firmware) that work together to provide a seamless user experience.
To enable and improve the interoperability of the EUDI Wallet across European Union countries, the eIDAS expert working group created the ARF document, aiming to:
- Provide all the specifications needed to develop an interoperable EUDI wallet solution based on common standards and practices
- Provide a state-of-play of the eIDAS Expert Group’s ongoing work
- Form the basis of the reference implementation of the EUDI project and support the EU Commission’s large-scale pilots.
Key challenges of ensuring security for the EUDI Wallet

“A technology where we can control ourselves what data is used and how.” Ursula von der Leyen, President of the European Commission.
With the introduction of the EUDI Wallet eIDAS v2.0, security will be of prime importance to ensure a high eIDAS assurance level, so that solutions can be trusted by governments, businesses and end-
users. The following key challenges also need to be addressed:
1. The EUDI Wallet is a new attractive target for cyberattacks
The EUDI Wallet will become a technological centerpiece, enabling several use cases as identified in the ARF:
- Secure and trusted identification to access online services
- Mobility and digital driving license
- Healthcare credentials
- Education credentials
- Professional qualifications
- Digital finance
- Digital travel
Many of the above use cases are traditionally secured with smartcards certified at Common Criteria level EAL4+ with VAN.5, and the EUDI Wallet will need to provide an equivalent level of security.
Main challenge: Providing an end-to-end solution for the EUDI Wallet that will secure its lifecycle, environment, components, usage, and integration within the mobile phone.
2. Citizen data shall be protected and meet GDPR regulation while ensuring user consent.
The level of security should ensure confidentiality, integrity and privacy of the EUDI Wallet. While several EUDI Wallet implementations can be deployed as described in the ARF, not all implementations are offering a similar level of security for confidentiality, integrity and privacy.
As an example, mobile phone-enabled Secure Elements (SEs), which are certified as meeting EAL5+, will offer the EUDI Wallet local citizen data storage. However, other solutions might require remote handling of citizen data, where the security objectives of confidentiality, integrity and privacy will need to be covered.
Main challenge: Providing a solution for the EUDI Wallet that covers the security aspects of confidentiality, integrity and privacy, while maintaining the user’s consent. It will be important to avoid the centralization of citizen data, which could become attractive to a nationwide attack.
3. Security certification standards and guidelines shall be identified
A standardized approach to certification will be important to ensure all wallet implementations are interoperable, and provide an overall level of security compatible with eIDAS security level high.
The European Commission has acknowledged the need to identify a toolbox that will meet these needs. Here there are three streams to consider. One is that several solutions already exist, with proven records such as PP0084 EAL4+ with VAN.5 for Secure Element, CSP applet Protection Profile, etc.
The second element is those technologies that are not already available and certified to meet the required levels of security and interoperability; such as key management, lifecycle management, security of specific hardware and others.
The final consideration is the security of specific hardware and software components that will play a role in the EUDI Wallet as supportive elements (NFC, UWB, mobile phone OS, etc.).
Main challenge: Define standards and guidelines for the EUDI Wallet to enable harmonization and interoperability of the solutions.
4. EUDI Wallet lifecycle management
The EUDI Wallet lifecycle management shall cover all aspects of the wallet, from the manufacturing, enrollment, application installation, activation and deactivation of wallet, product update and product retirement, as traditional lifecycle events.
This will also include lifecycle events more traditionally related to the mobile phone usage and the citizens such as acquiring a new phone, delegating the wallets (for example in the context of a family), updates to citizen information and transportability.
Main challenge: Define EUDI Wallet lifecycle management covering all the lifecycle steps in a meaningful way while ensuring the security at each stage.
5. Mobile phones are subject to many updates
Mobile phones are subject to many updates. Frequent software and firmware releases, new features, bug corrections and security patch updates are dynamic and occur on a regular basis.
On a positive side, those updates are enabling a security continuity of the product and reducing the window of opportunity for an attacker.
The negative side to this is that systems not kept up-to-date or not updated as soon as new versions are available can present opportunities for attacks.
Main challenge: Ensure that all critical updates are being released on a timely basis to maintain the system security and EUDI Wallet key secrets, whilst ensuring the introduction of new critical updates on the mobile phone does not impact the security level of the EUDI Wallet and that functionality remains the same.
6. The EUDI Wallet cryptography shall be post-quantum resistant
As EUDI Wallets will be used by citizens to perform sensitive digital administrative activities, the implementation of post-quantum resistant cryptography is of major importance.
Increased usage of the EUDI Wallet and associated sensitive data, as well as the transfer of data between stakeholders traditionally protected with strong cryptography are at risk of data harvesting. Here the decryption of this sensitive data would represent a future threat when quantum computers become available.
Main challenge: Ensure that EUDI Wallet cryptography is post-quantum resistant.
7. The EUDI Wallet will maintain security operations while the mobile phone is out of battery or out of network
As the EUDI Wallet is aiming to offer similar usage as traditional ID documents, it should remain available to users even when offline, to ensure its usage isn’t restricted to areas with Wi-Fi, or mobile network connections EUDI Wallet. When offline, and in cases where the phone is out of battery, it will be important to maintain security.
Main challenge: Ensure the availability and security of the EUDI Wallet in the context of the mobile phone being out of battery or out of network.
SESIP evaluation methodology and the EUDI Wallet ecosystem
In this section we will review why SESIP is a good fit for the EUDI Wallet ecosystem.
1.SESIP is designed for accessibility
The SESIP evaluation methodology has been designed for accessibility, with the objective that the results of an evaluation must be accessible and useable by security-proficient developers without the need for evaluation expertise.
Additionally, SESIP incorporates a set of Security Functional Requirements (SFRs) that are a perfect fit for the EUDI Wallet, which include, but are not limited to:
- Identification and attestation of platforms and applications
- Lifecycle management, covering aspects of secure boot, product updates, secure installation, and others
- Identity of the device, including platforms, applications and platform components
- Cryptographic functionality
- Compliance functionality, covering secure storage, audit log, debugging and others.
2. SESIP is designed for reuse and composition
SESIP has been designed to enable reuse and composition of evaluation results for security certifications, so that previously certified components can be reused to simplify future evaluation processes for new solutions.
The SESIP evaluation methodology provides guidelines for the reuse and composition of evaluation results and has been used already for recognized industry certifications such as ISO/IEC 62443, ISO21434, WPC Secure Storage Subsystem, ISO26262 and others.
Additionally, SESIP covers the composition of evaluation, for example an evaluation of a software applet running on top of a Common Criteria EAL5+ hardware which results in a simplified evaluation approach.
3. SESIP Protection Profiles are easy to create, fostering harmonization and making them an ideal target for mobile phone components supporting the EUDI Wallet
SESIP has been designed for accessibility. One key feature is the ability to easily create a SESIP Protection Profile which fosters harmonization. The creation of SESIP Protection Profile that is designed for a specific component allows a strict formalism of the key essential features, and in a language that can be understood by all stakeholders involved in the development and usage of the specific component. Supporting the harmonization of components that play a supportive role in the EUDI Wallet will ensure end to end security.
Let’s look at it in practice. The following diagram represents an EUDI Wallet architecture proposed by the ARF document prepared by the eIDAS expert working group.
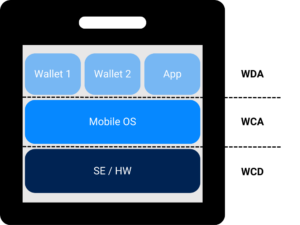
Wallet Secure Cryptographic Device (WCD)
The security of the layer of WCD is traditionally covered by several hardware and software components that are certified with Common Criteria EAL5+ as the state-of-the-art of security in the industry. However, other elements of the WCD are not covered as extensively, despite playing an important role in security as supportive elements.
SESIP can map security requirements to address the communication layer such as NFC and UWB. The creation of SESIP Protection Profiles for this specific communication layer will allow a step-up in security as well as their integration within the mobile phone to protect against misuse.
Wallet Creation Application (WCA)
The Wallet Creation Application layer can strongly benefit from SESIP, as it can cover evaluation of the mobile phone Operating System and the middleware. SESIP Protection Profiles created for these components can cover all security aspects related to EUDI Wallet lifecycle management, management of the user data, key security features, product updates and others. This Protection Profile will be a composition with the WCD certification.
Wallet Driving Application (WDA)
A SESIP Protection Profile could be used to support the Wallet Driving Application in demonstrating compliance of the applet with the intended use cases, and leveraging the reuse of evaluation results.
Security levels to establish trust across EUDI
The scope of use cases for EUDI Wallet is ambitious. It needs to support a wide range of services, whilst storing and managing sensitive personal data. To ensure this is delivered with trust across the EU, testing and certification processes must be established for the various hardware and software components of a mobile phone.
The SESIP methodology can address this complexity, enabling the reuse of certifications for individual parts, to allow a certification by composition approach. This will simplify the certification process and bypass the need for individual testing and evaluation of previously certified parts. SESIP maps to the functional security requirements of existing schemes, to provide a more holistic view of the security of an entire solution or device, rather than just those that relate to individual parts.
Through SESIP, its certification processes and experience in developing standardized secure technologies, GlobalPlatform can help decision makers meet the security challenges of the ambitious EUDI Wallet project, and give options to regulators. Find out about how each of GlobalPlatform’s offerings can support EUDI in this white paper.

