The evolution of European regulations and how SESIP can support the ecosystem
As GlobalPlatform prepares to host its next seminar on SESIP (Barcelona and virtually, October 19), Carlos Serratos, IoT Certification Expert at NXP, explains how the methodology can empower the European goals of building a cyber resilient society.
The 21st Century is defined by the digital transformation of societies. Digitalization touches every aspect of our lives, from the day-to-day activities with our conveniently smart devices, to supporting nations and infrastructures that are subsequently delivering those services throughout society.
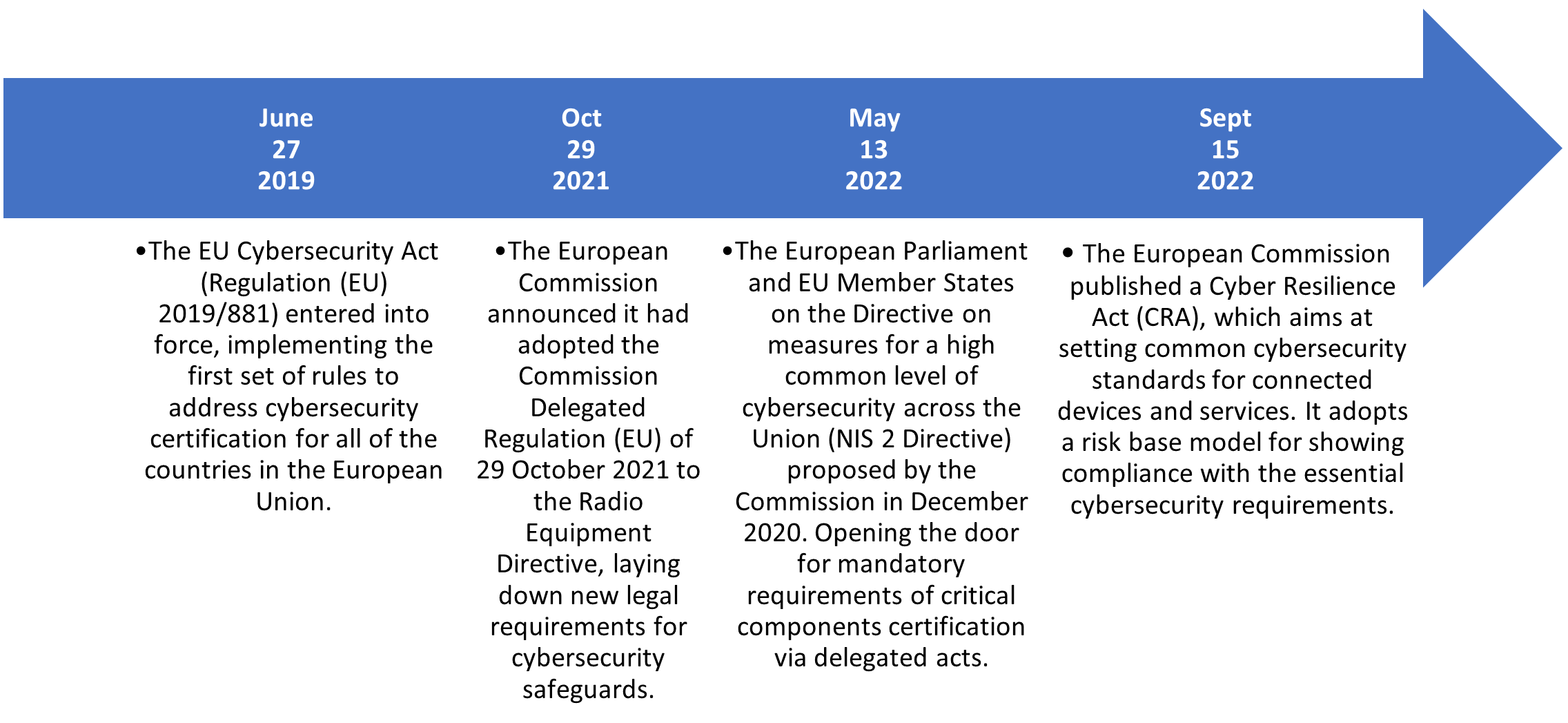
Making sure that European citizens can rely on, and trust digitalization has been one key objective of the European Commission. Providing pieces of legislation to support this goal is nothing new and it has been a non-wavering effort over the last few years that will only continue as we move even further into a digital-first future. Some key dates of note are below:
Those regulations, and some more, share common principles. For example:
- A component is part of a bigger system. Sometimes, the system is understood as a complex system with backends and more, where the IoT device is seen as component. Sometimes, the device itself is the system, however, either way, a system has components.
- Systems, and components need to show State of The Art (SOTA) features. But SOTA doesn’t mean the latest or the greatest on security technology, it means that the device, component and system provides security countermeasures with robustness that are proportional to the risk. For example, a router might be recognized as SOTA for a home application, but not necessarily recommended for critical infrastructure.
- The chain is as strong as the weakest link. Therefore, it’s important to identify and recognize the key security components providing the core security capabilities.
- There might be several ways to show conformance and security certifications are a way to demonstrate this.
- The legislation recognizes that a cyber incident might be impossible to prevent as technology and the threat landscape evolves rapidly. Therefore, the focus is on suppliers and operators to show due diligence by making sure they have the SOTA required, and certification is a recognized way to do so.
And this is where the Security Evaluation Standard for IoT Platforms (SESIP) methodology embraces those principles. For example:
- IoT devices and platforms are the result of a combination of smaller parts providing the core security capabilities. Starting with a Root of Trust that will support the software layer, such as the Operating System (OS), with core security capabilities. In turn, OS might add new security functionality and expose the security services to other software layers until reaching the application layer. This approach is called ‘composition’ which is at the core of SESIP.
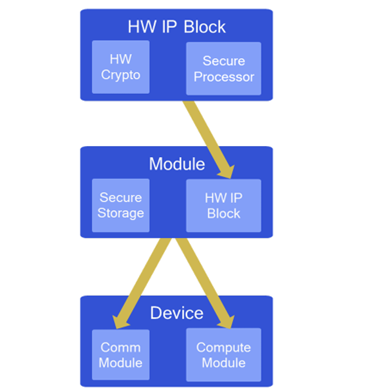
- As a methodology oriented to IoT devices, SESIP provides the evidence of SOTA by mapping the results of the evaluations against five different levels of resistance and assurance. In turn, this helps IoT developers to identify and demonstrate the right technology is being utilized for their use cases.
- SESIP evaluations provide evidence of the components’ security capabilities - which are either individually or combined (composed) in IoT platforms.
- This core set security capabilities can be mapped to the device requirements from policies, schemes, and standards as a show of conformance with those requirements.
- The security evaluations of compositions focus on the proper integration of the components using integration guidelines, which are also part of the security evaluation.
SESIP is a candidate to become a European Norm (EN) under CEN/CENELEC. This will facilitate the adoption and recognition of the evaluation results which show evidence of conformance, due diligence and proper use of SOTA technology – all of which help to support the European goals of building a cyber resilient society.
If you want to know more about SESIP, security regulatory compliance and the latest trends in those areas, join us for the SESIP Seminar, in Barcelona (and virtual) on October 19. Alongside presentations from organizations including Microsoft, Arm and AWS, there will be panel discussions and use case examples of the SESIP methodology in action.
View the agenda and register here.
Watch this video to hear first-hand from Carlos on how SESIP is optimizing security evaluation in the IoT.

